¶ LWM2M authentication with certificates
Below you will find information about how to connect to the Tartabit IoT Bridge using a LWM2M client with certificate based authentication.
¶ Certificates with thumbprints
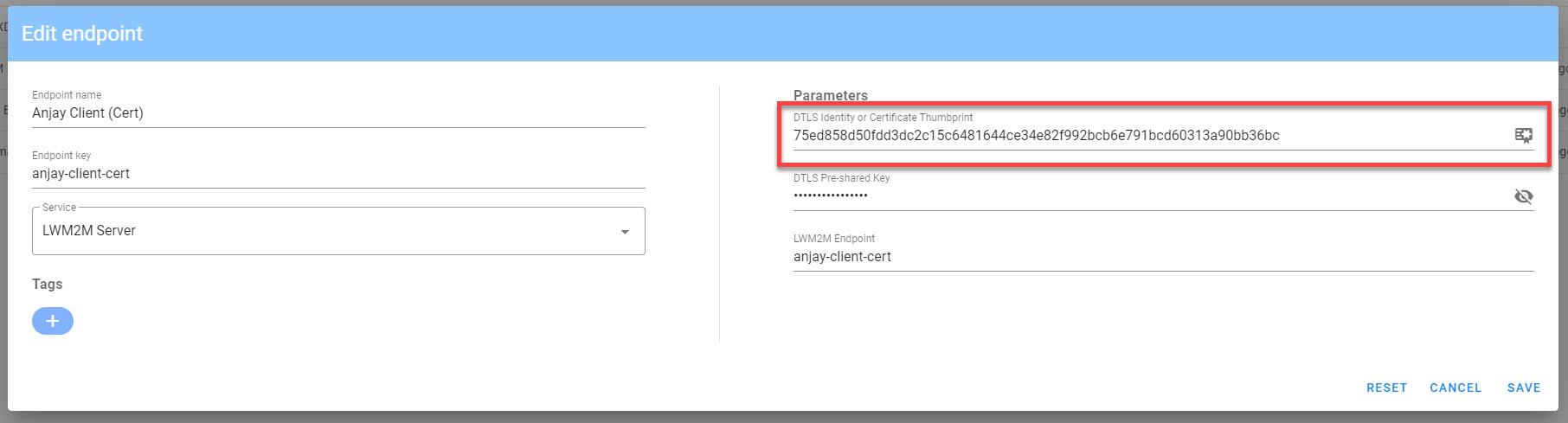
When using thumbprints, each Endpoint in the IoT Bridge is configured with the thumbprint of the certificate associated with the device. This enables fine control over which devices can connect, but it also requires provisioning the security information for every device that attempts to connect.
¶ Generate certificate pairs with openssl
# generate the private key
openssl ecparam -out client.key.pem -name prime256v1 -genkey -noout
# convert the private key from pem to der format (needed by some clients)
openssl ec -in client.key.pem -outform DER -out client.key.der
# generate the certificate
openssl req -new -key client.key.pem -x509 -nodes -days 2650 -out client.cert.pem
# convert the certificate from pem to der format (needed by some clients)
openssl x509 -in client.cert.pem -outform DER -out client.cert.der
¶ Adding a thumbprint to an endpoint
The thumbprint can be added manually, or by clicking the certificate icon and selecting the PEM encoded certificate from your filesystem.
¶ Certificates with a common CA
Use a CA to authenticate all certificates that have been signed by the same CA. Currently the CA method requires a single CA certificate that directly signs the client certificates, use of intermediate CAs is not supported. Additionally, each CA certificate is identified uniquely by its Distinguished Name (DN) must have a globally unique DN or else an error will be reported. As such, the same CA certificate, or a CA certificate with the same DN as an existing certificate cannot be used in multiple accounts.
If you see an error in the logs "Certificate is already in-use", that means that the DN for the certificate you are trying to use has already been registered into another account.
¶ Generate root CA with openssl
# generate the root private key
openssl ecparam -out root.key.pem -name prime256v1 -genkey -noout
# generate the root cert
openssl req -new -key root.key.pem -x509 -nodes -days 3650 -out root.cert.pem
¶ Generate a signed client certificate
# generate the leaf key
openssl ecparam -out leaf.key.pem -name prime256v1 -genkey -noout
# convert the leaf private key from pem to der format (needed by some clients)
openssl ec -in leaf.key.pem -outform DER -out leaf.key.der
# generate the leaf csr
openssl req -new -key leaf.key.pem -out leaf.cert.csr
# generate leaf cert
openssl x509 -req -in leaf.cert.csr -CA root.cert.pem -CAkey root.key.pem -CAcreateserial -days 3650 -sha256 -out leaf.cert.pem
# convert the leaf certificate from pem to der format (needed by some clients)
openssl x509 -in leaf.cert.pem -outform DER -out leaf.cert.der
¶ Verify a certificate is signed by a CA
openssl verify -verbose -CAfile root.cert.pem leaf.cert.pem
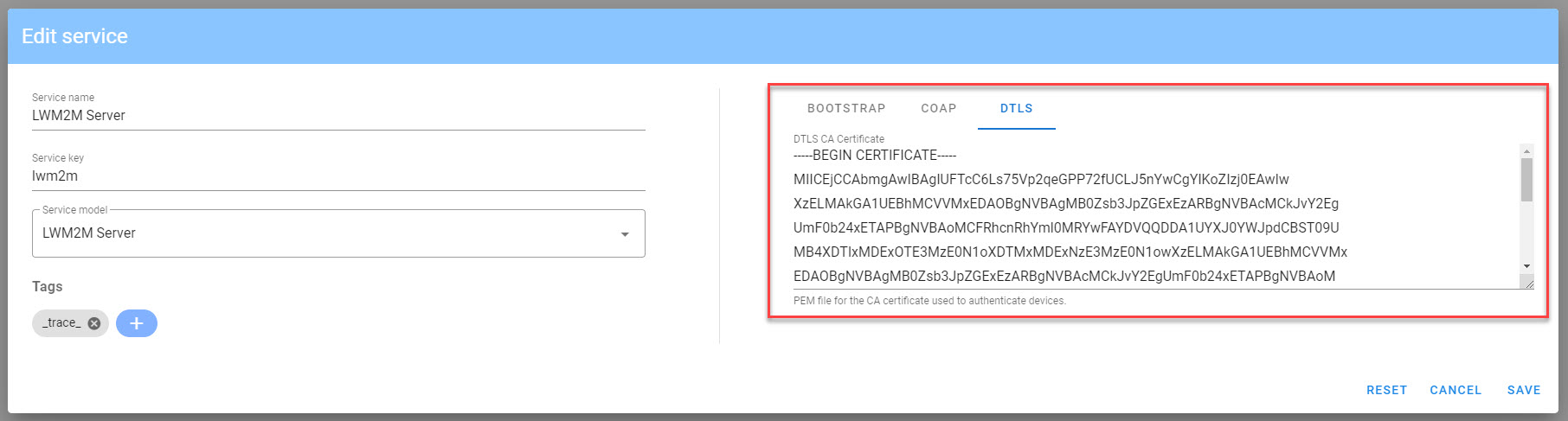
¶ Configure a LWM2M Service with a CA
The CA certificate should be pasted into the service definition, make sure to include the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- blocks.